背景介绍
在前一节主要介绍了Glibc的堆内存管理的机制,在上一节的基础上,我打算介绍一下针对Glibc堆内存管理的攻击。此系列我打算按攻击面是哪一个bin来展开,主要分为:
- fastbin的攻击
- smallbin的攻击
- largebin的攻击
- unsorted bin的攻击
top chunk的攻击
本文主要介绍fastbin的攻击
fastbin漏洞利用
具体的fastbin的介绍请参考前一节和 Linux堆内存管理深入分析(下),在本节中主要结合how2heap的代码来介绍一下具体的漏洞利用思路。
fastbin double free
double free的意思就是一个malloc的指针被释放了两次,由于针对fastbin的free处理只是对double free做了简单的判断,所以很容易绕过它的double free判断。free() fastbin时的判断如下所示:
1 | /* Check that the top of the bin is not the record we are going to add |
其中old指针为fast bin的头指针,即此处只是判断fastbin的头指针和p指针是否一致。所以fastbin double free的攻击思路就是我们只要保证要double free的chunk不在fastbin的头部即可。
具体的攻击示例如下:
1 |
|
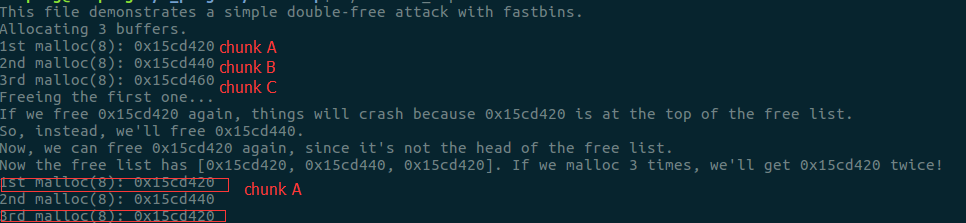
在此示例中,首先申请三个大小为8的int数组,然后先free(a),由于fast bin是一个单链表,在插入和删除的时候只在头部进行,所以此时将a的chunk放入了fast bin的头部,随后又free(b),此时fast bin的头部为chunk b,随后又free(a),此时由于fast bin的头部为chunk b,所以在free()的时候进行判断old == p不会抛出错误进而绕过这个简单的判断处理。再进行malloc的时候首先会从fast bin的头部进行删除,则接下来第一个分配的chunk为chunk A,第二个分配的为chunk B,接下来会再次分配chunk A。
绕过示例结果如下所示:
fast bin double free in stack
上面的那个例子只是简单的一个double free,这个例子是利用double free漏洞在栈中构造了一个fake chunk。
其具体的示例如下所示:
1 |
|
在以上代码中,当d被malloc的时候,此时还有对应的chunk a在fast bin中,所以如果对d进行修改,也会影响到chunk a的值。我们知道malloced chunk和freed chunk对应的结构不一样,对与同一个chunk A来说,有两种形式–对于d来说,其对应的是malloced chunk,而其在fast bin中还有一个freed chunk。
其示例如图所示:
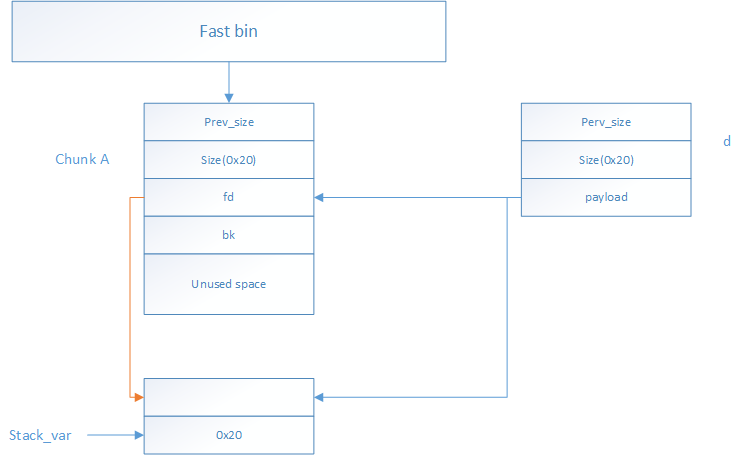
可以看到d(payload开始地址)正好对应了chunk A的fd指针,将 d的值赋值为&stack_var-8,则 stack_var=0x20即为在栈中伪造的chunk的size=0x20,与此fast bin的大小对应,此时chunk A的fd指向了在栈中伪造的chunk,此时就将伪造的chunk放入了fastbin链表中。进而malloc可以返回伪造的指针。
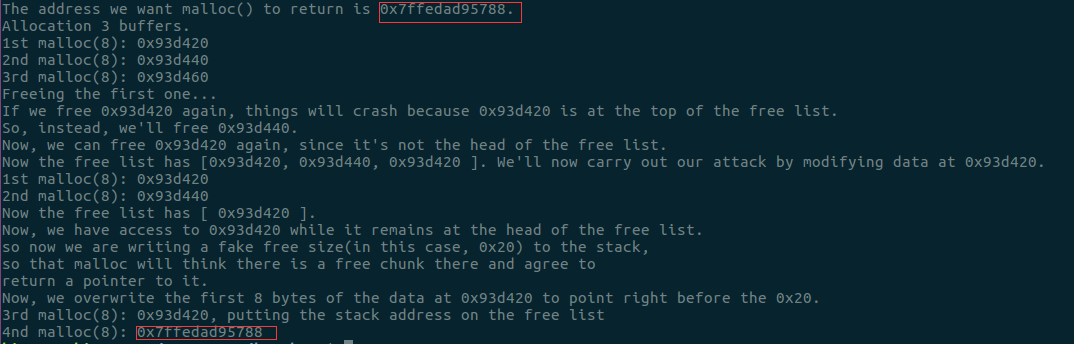
该示例代码的运行结果如下所示:
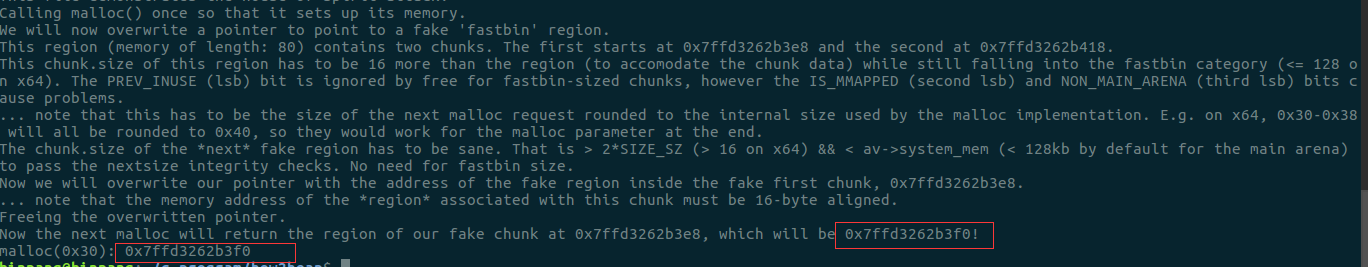
The house of spirit
此攻击也是在栈中伪造fake chunk,和第二个攻击不同的是其只是在栈中声明了一个指针,而并没有通过malloc()函数来在堆中申请空间,接着将该指针赋值为特定的伪造的chunk的地址,随后free该指针,就将在栈中伪造的chunk添加到对应的fastbin中去了。具体的示例如下所示:
1 |
|
示例的结果如下图所示: